keywords
Huaxin International Investigation (HII)Investigation Services in China
1 Introduction
Web browsers are used on a daily basis to perform many various online activities, such as searching for information, shopping and conducting payment transactions. Web browsers log and store a large amount of data concerning users’ browsing activities, including caching files, visited URL’s, search terms and cookies. These are retained on the user’s computer and are easily located by other users. The use of a browser’s public mode therefore facilitates a digital forensic investigator’s examination of a suspect’s internet activities, as is needed in cases where questionable web sites were visited or criminal acts were conducted through the Internet. However, over the past few years, vendors of the major web browsers have expressed concern over users’ privacy while browsing the Internet. This has entailed their development of a new feature, the “private browsing” mode, with the aim of enabling users to browse the Internet whilst leaving no trace of their browsing activity. Although private browsing modes may be deployed by some users for a variety of respectable reasons, such as buying a surprise gift, they can also be exploited by cyber criminals for nefarious activities. The endeavours of these criminals to thoroughly erase any evidence of their Internet browsing activities seem to be facilitated by the private browsing modes. For example, they can prevent the inscription of an individual’s private browsing data on the hard drive, assisting criminals by leaving none of the evidential artifacts which can be vital in a court of law.
This paper aims to investigate the effectiveness of the private browsing modes built into four major Internet browsers: Google Chrome Incognito, Mozilla Firefox Private Browsing Mode, Internet Explorer InPrivate and Apple Safari Private Browsing Mode. To achieve this, a set of identical experiments is carried out on private browsing mode of each of the four web browsers, using selected pre-defined web browsing activities. The forensic analysis is conducted in two stages. Firstly, the analysis is performed on both “common” and “uncommon” locations on the hard drive; and the second stage involves investigating Physical Memory (RAM). This is to investigate whether each browser, while in private mode, leaves browsing artifacts or not in these locations.
2 Literature Review
Private browsing modes have different names according to the browser. It is called “Incognito Mode” in Chrome [1], “InPrivate Browsing” in Internet Explorer [2], “Private Browsing” in Firefox [3] and “Private Browsing” in Safari [4]. “Private Browsing” was first released by Apple Safari in 2005 [5]. Following the same principle Google Chrome and Microsoft introduced “Incognito” and “InPrivate” respectively in 2008 [6]. Mozilla’s “Private Browsing” was introduced in 2009 [7]. The most common reasons cited by vendors for providing private modes are to enable shopping for surprise gifts on a family PC [2] and the planning of surprise parties [1]. However, through their research work, Aggarwal et al. [8] revealed that in reality the searching of adult websites was the primary reason for utilizing private modes [8]. Using a particular technique, Aggarwal et al. [8] posted advertisements on ad-networks to target various categories of websites including adult and gift websites “to correlate the use of private mode with the type of website being visited”. This experiment revealed that private browsing was more popular at adult sites than gift buying websites.
Two distinct goals must be met in order for a private mode to be considered safe and secure. The first goal is security against a local attacker (“an attacker who controls the user’s machine”) and the second goal is security against a web attacker (“an attacker who controls websites the user visits”) [8]. Regarding the local attacker, while in private mode browsers should be able to prevent the sites visited from placing browsing artifacts on the user’s machine. For web attackers, browsers should make it impossible for websites to find out whether a particular user has previously visited them by preventing websites from linking users’ activities whilst in private and public modes. Although the web attacker model has been previously researched to some extent [8, 9, 10], the concept of the local attacker has not been addressed adequately. No paper was found that investigates private browsing modes except the research conducted by Said et al. [12]. However, Said et al’s [12] results cannot be considered accurate as they conducted their experiments on a polluted system. Moreover, they carried out their experiments on older versions of the web browsers’ private modes. Therefore, it was decided to conduct new experiments to provide a better understanding of this phenomenon and to find out how this feature could affect digital forensic investigations.
3 Testing Methodology
Web browsing activities plan detailed below was designed to emulate a realistic scenario in which a cyber-criminal or suspect carries out one of the following actions:
-
1.
Use of the browser to visit www.youtube.com; entering the search term “jessie ware wildest moments” and watching the video.
-
2.
Use of the search engine ‘Google’ to find and visit the “Pirate Bay Proxy,” then searching for “Ubuntu” on this website, but taking no further action.
-
3.
Visiting www.facebook.com and downloading a profile picture.
-
4.
Visiting www.amazon.co.uk and searching and viewing “Casio F-91W”.
-
5.
Using Google, searching and viewing, but not saving, a PDF file titled “Doppelganger: Better Browser Privacy without the Bother.”
The aim of these tests was to investigate the effectiveness of the private browsing modes of the four widely used web browsers and to find out whether artifacts of the tests carried out could be found. Experiments on the “private” modes were conducted on the below versions of the four browsers as follows. Note that although the experiments were conducted on the private modes of the older versions of the browsers, the problem associated with the security of these private modes still remain.
-
Incognito – Google Chrome Version 26.0.1410.43.
-
Private Browsing – Mozilla Firefox Version 20.0.
-
InPrivate – Internet Explorer Version 9.0.8112.16421.
-
Private Browsing – Apple Safari Version 5.1.7 (7534.57.2).
The presented set of browsing activities was run identically on the snapshots of the virtual machine in the private browsing modes in order to determine whether any of the following browsing artifacts could be recovered; cached web pages, web browsing history, download history, visited URLs, search terms used in the Google search engine or website search options. In the search for browsing artifacts, images of Physical Memory (RAM) were also captured for analysis. Physical Memory contains volatile data which can be lost once the machine is switched off. Therefore, the decision to investigate RAM was made with a view in emulating a realistic police raid scenario, where officers must carry out a live investigation of the suspect’s machine before turning it off and removing it for further analysis.
3.1 Platform Options - Virtualization
In order to ensure that the experiments would be conducted on a clean system to avoid polluting the research by mixing browsing artifacts, various options were considered. It was decided to utilize virtualization, and VirtualBox was selected as it is freely available and has open-source software and a virtual hard disk which can be forensically imaged using AccessData’s FTK Imager. It was decided to utilize snapshots as the preferred method and was adopted for all the experiments conducted for this project. The reason for this choice was because snapshots would require the setting up of only one base virtual machine from which multiple snapshots could be taken each taking only a few seconds. Once each experiment was completed, the snapshot of the virtual machine was closed and the snapshot was restored to its preceding, original state.
In order to prevent the pollution of the experiments, each web browser was installed in separate virtual machines using its installer, which was transferred without using another browser to download (such as Internet Explorer). This ensured that no browsing artifact was left behind when experimenting on other browsers. Using VirtualBox, it was possible to set up a shared folder between the host machine (the physical machine on which VirtualBox ran) and the guest machine (the virtual computer running inside VirtualBox). In order to carry out the hypothetical digital forensic investigation, various software and tools were utilized. These included: (1) FTK Imager version 3.1.2, (2) Autopsy 3.0.4, (3) FTK 1.81.6 and (4) WinHex.
4 Results
Identical test was performed on each web browser’s private mode inside its respective snapshot of the virtual machine. Upon the completion of each experiment and prior to closing down a particular web browser’s private mode, RAM was imaged and verified through matching MD5 and SHA1 checksums using FTK Imager 3.1.2. The private mode session was then terminated by closing down the private browsing window. Using FTK Imager again, the virtual hard drive of the snapshot was then imaged and verified through corresponding MD5 and SHA1 checksums.
The first part of the analysis involved the examination of different locations on the hard drive image. The hard drive image of each snapshot was separately imported to Autopsy and FTK for examination. Four different cases were then built for four different experiments on the private browsing modes. Both “common” and “uncommon” locations on the hard drive were analyzed to identify whether traces of the browsing activities carried out in private mode could be found.
The second part of the analysis required examination of the captured image of the RAM of each snapshot for each particular experiment on the private browsing mode. As with the hard drive examination, four different cases were built for four different experiments on the private browsing modes. FTK 1.81.6 and WinHex were deployed for the examination of the RAM images due to their useful and powerful capabilities. In this way, the RAM images were analyzed to search for any browsing artifacts from the experiments on the private mode sessions.
4.1 Common and Uncommon Locations
The first part included the examination of different locations on the captured image of the hard drive including “common” and “uncommon” locations where the browsers store web browsing history and cache. Neither “common locations” (Cache folder, Web history) nor “uncommon locations” (“$MFT”, “$LogFile”, “Favicons”, “etilqs”, “Manifest.json”, “pagefile.sys.”, “unallocated space” and “slack space”) revealed any trace of browsing artifacts in Chrome browser. In Firefox, no traces were found in “common locations” or “uncommon locations” (including “places.sqlite”, “webappsstore.sqlite”, “sessionstore.bak”, “search.json” and “nssckbi.dll”). However, on investigating the “pagefile.sys”, some entries were discovered relating to pre-defined web browsing search terms used during the private browsing session. The findings were as follows (Table 1):
Table 1.
Entries related to search terms discovered from pagefile.sys.
|
Search term |
Entries |
|---|---|
|
‘Pirate Bay Proxy’ |
1 |
|
‘Ubuntu’ |
3 |
A profile picture downloaded from “www.facebook.com”, while in Mozilla Firefox’s private browsing mode, was discovered. Firefox had unexpectedly retained this picture. Using the “data carving” technique, profile picture was recovered. This finding contradicts the claims of Mozilla’s vendor that Firefox deletes any downloaded item after the termination of a private browsing session [7].
Unlike the tests of the first two web browsers, examination of Internet Explorer’s “Cache” records revealed many traces of the pre-defined web browsing activities, despite the browsing activities being undertaken in its “private” browsing mode. All the traces of the browsing artifacts from private browsing session had leaked into the “Cache” folder. For example, the visited URLs, search terms, downloaded picture and PDF file viewed could all be seen in the “Cache” folder.
Although many of the files containing the web browsing artifacts within the “Cache” folder were intact, Internet Explorer had deleted some of them. It appears that Internet Explorer caches the browsing artifacts on the hard drive and “deletes” them when the private browsing session is terminated. However, it does not “erase” the browsing data, thus files remain on the hard disk until they are overwritten by other files. Therefore, a forensic investigator would be able to recover those files if he were analyzing a machine at the state where the files containing the browsing data had been deleted but not yet overwritten. This was confirmed by the recovery of the deleted files using the “data carving” technique on the entire “Cache” folder. Executing data carving on the “Cache” folder using the FTK surprisingly recovered all the deleted artifacts that were contained in those files. Below are the findings after analyzing the “Cache” folder (Fig. 1and Table 2):
Open image in new window
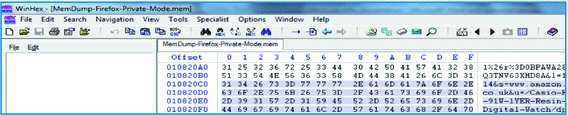
Fig. 1.
Firefox browsing data from private browsing session recovered from the RAM, showing the website www.amazon.co.uk visited and the entered keywords “Casio F-91 W”
Table 2.
Entries for visited URLs and search terms used in InPrivate mode found in Cache.
|
Visited URL |
Entries |
|---|---|
|
www.youtube.com |
19 |
|
www.facebook.com |
27 |
|
www.google.com |
132 |
|
www.amazon.co.uk |
276 |
|
Search term |
Entries |
|---|---|
|
‘jessie ware wildest moments’ |
84 |
|
‘Pirate Bay Proxy’ |
102 |
|
‘Ubuntu’ |
32 |
|
‘Casio F-91 W’ |
96 |
|
‘Doppelganger: Better Browser Privacy…, the entire PDF file could be found in the “Cache”’ |
6 |
|
Picture downloaded from www.facebook.com |
Entries |
|---|---|
|
“Profile Picture” |
1 |
Next “common location” investigated was Internet Explorer’s “Web History”. Although this was not as rich as the “Cache” folder in terms of browsing artefacts, an analysis nevertheless revealed some traces relating to a search term for the PDF file and an entry for the downloaded picture during the private browsing session. Entire PDF file could be seen, despite the fact that it had only been viewed and not downloaded, as specified in the pre-defined web browsing activities. Indeed, the full PDF file was recovered. Below shows the findings after analyzing the “Web History” of Internet Explorer (Table 3).
Table 3.
The analysis of Web History revealing the full path to the location of the downloaded picture and PDF on the hard drive image.
|
Downloaded picture |
Entries |
|---|---|
|
/img_HDImage-Internet-Explorer-Private-Mode.001/vol_vol3/Users/XXXX/Downloads |
1 |
The next stage in analyzing the hard drive image was an examination of the “uncommon locations”. These included “ntuser.dat”, “$Unalloc” “$MFT”, “pagefile.sys”, “search.js”, “iframe.js” and “schema.dat”. The followings are the findings after analyzing these “uncommon locations” (Tables 4 and 5).
Table 4.
Search terms used in InPrivate mode discovered in uncommon locations $MFT and unallocated spaces.
|
Search term discovered in $MFT |
Entries |
|---|---|
|
‘jessie ware wildest moments’ |
19 |
|
‘Casio F-91 W’ |
3 |
|
‘Doppelganger: Better Browser Privacy without the bother’ |
1 |
|
Search term discovered in pagefile.sys |
Entries |
|---|---|
|
‘Ubuntu’ |
2 |
|
Search term discovered in search.js |
Entries |
|---|---|
|
‘jessie ware wildest moments’ |
23 |
|
Search term discovered in unallocated spaces |
Entries |
|---|---|
|
‘jessie ware wildest moments’ |
65 |
|
‘Pirate Bay Proxy’ |
59 |
|
‘Ubuntu’ |
148 |
|
‘Casio F-91 W’ |
52 |
Table 5.
Internet Explorer, while in private mode, had leaked the PDF file into $Logfile.
|
PDF file |
Entries |
|---|---|
|
doppelganger-ccs06[1].pdf |
5 |
In Safari the hard drive image was examined by searching the “uncommon locations” which included “WebpageIcons.db”, “pagefile.sys”, “_k.cfs”, “search.js”, “ieframe.dll.mui”, “schema.dat”, “Data1.cab”, “e4e8be02b8faeta7_blobs.bin” and “LastSession.plist”. No trace of browsing artifacts was discovered in any of these “uncommon locations,” except in “WebpageIcons.db” and “e4e8be02b8faeta7_blobs.bin”. All traces of browsing artifacts regarding the “pre-defined web browsing activities” conducted in the private browsing mode of Apple Safari could be seen in this “uncommon location”. The findings were as follows (Table 6):
Table 6.
Search terms used in Apple Safari’s private mode discovered in WebpageIcons.db and e4e8be02b8faeta7_blobs.bin.
|
Search term discovered in WebpageIcons.db |
Entries |
|---|---|
|
‘jessie ware wildest moments’ |
6 |
|
‘Pirate Bay Proxy’ |
18 |
|
‘Ubuntu’ |
7 |
|
‘Casio F-91 W’ |
7 |
|
‘Doppelganger: Better Browser Privacy without the bother’ |
3 |
|
Search term and PDF discovered in e4e8be02b8faeta7_blobs.bin |
Entries |
|---|---|
|
‘Casio F-91 W’ |
3 |
|
doppelganger-ccs06[1].pdf |
1 |
A subsequent investigation of “unallocated spaces” revealed that they too were rich in their storage of the browsing artifacts left behind from Safari’s Private browsing mode. The findings after analyzing “unallocated space” were as follows (Table 7):
Table 7.
URLs visited and search terms used in the private mode recovered from $Unalloc.
|
Visited URL Discovered in $Unalloc |
Entries |
|---|---|
|
www.youtube.com |
45 |
|
www.facebook.com |
27 |
|
www.google.com |
15 |
|
www.amazon.co.uk |
1 |
|
Search term discovered in $Unalloc |
Entries |
|---|---|
|
‘jessie ware wildest moments’ |
16 |
|
‘Pirate Bay Proxy’ |
28 |
|
‘Ubuntu’ |
18 |
Table 8.
The number of entries found in the RAM for each pre-defined web browsing activity carried out in the private browsing mode of each web browser.
|
Web browsing activity |
Chrome |
Firefox |
IE |
Safari |
|---|---|---|---|---|
|
Visited URL “www.youtube.com” |
1,180 |
204 |
504 |
4,038 |
|
Visited URL “www.google.com” |
1,611 |
210 |
1,053 |
2,142 |
|
Visited URL “www.facbook.com” |
1,764 |
396 |
5,757 |
7,077 |
|
Visited URL “www.amazon.co.uk” |
1,719 |
760 |
3,292 |
11,744 |
|
Search term “Jessie ware wildest moments” |
412 |
412 |
488 |
1,416 |
|
Search term “Pirate Bay Proxy” |
906 |
330 |
2,697 |
1,281 |
|
Search term “Ubuntu” |
197 |
164 |
330 |
665 |
|
Search term “Casio F-91W” |
268 |
216 |
780 |
8,253 |
|
Search term “Doppelganger: Better …” |
2,586 |
2,232 |
264 |
12,552 |
|
Downloaded “profile picture” |
None |
None |
None |
3 |
Additionally, entries for the “profile picture” downloaded while in the private browsing session of Apple Safari were also discovered. For example, the image itself was found in the “Download” folder on the hard drive. The full path to this folder is as follows: /img_HDImage-Safari-Private-Mode.001/vol_vol3/Users/xxx/Downloads”. Moreover, there were enough traces left on the system to show that a Facebook profile “xxx” had been accessed during the private session. The traces of this browsing activity was found in many “uncommon locations” on the hard drive, such as “WebpageIcons.db” and “$Unalloc”.
4.2 Physical Memory (RAM)
The second part of the investigation involved an analysis of the captured images of the “Physical Memory” (RAM). After running a string search, both WinHex and FTK returned many hits on the URLs and search keywords used during the private browsing test. The below are the findings of analyzing the captured images of RAM:
5 Evaluation and Comparison of the Results
The aim of this phase was to provide a consistent evaluation environment in which to compare the results of the experiments performed on the “private” browsing modes of the four widely used web browsers. For simplicity, statistics are presented in tables. To minimize the amount of these tables, the number of entries found for each item of the pre-defined browsing activities is not given individually for each location. Instead, the total number of entries found in the different locations for that particular activity is provided. The exact amount of entries is detailed under the relevant sub-headings. Table 9 outlines the total number of entries found for a particular pre-defined web browsing activity and Table 10 lists the “common” and “uncommon” locations on the hard drive in which those entries were found. It is the results presented in these two sets of tables that are subsequently compared and evaluated to determine whether the private modes left traces of the pre-defined activities on the “common” and “uncommon” locations on the hard drive and whether traces were left in the same locations in the public and private modes.
Table 9.
The total number of entries found in different locations on the hard drive for each pre-defined web browsing activity performed during the “private” browsing session of each web browser.
|
Browsing activity |
Chrome |
Firefox |
IE |
Safari |
|---|---|---|---|---|
|
Visited URL “www.youtube.com” |
None |
46 |
74 |
63 |
|
Visited URL “www.google.com” |
None |
22 |
322 |
21 |
|
Visited URL “www.facbook.com” |
None |
7 |
259 |
47 |
|
Visited URL “www.amazon.co.uk” |
None |
3 |
514 |
19 |
|
Search term “Jessie ware wildest moments” |
None |
None |
191 |
22 |
|
Search term “Pirate Bay Proxy” |
None |
1 |
161 |
46 |
|
Search term “Ubuntu” |
None |
3 |
182 |
25 |
|
Search term “Casio F-91 W” |
None |
None |
151 |
10 |
|
Search term “Doppelganger: Better …” |
None |
None |
13 |
4 |
|
Downloaded “profile picture” |
None |
1 |
2 |
1 |
Table 10.
Various “common” and “uncommon” locations on the hard drive where the four web browsers left browsing artefacts while in “private” mode.
|
Web browser |
HDI - Common locations |
HDI - Uncommon locations |
|---|---|---|
|
Chrome |
None |
None |
|
Firefox |
Download folder |
ieframe.dll.mui places.sqlite |
|
IE |
Cache Web history |
ieframe.dll.mui pagefile.sys schema.dat search.js $Logfile and $Unalloc $MFT |
|
Safari |
Download folder |
e4e8be02b8faeta7_blobs.bin WebpageIcons.db $Unalloc |
5.1 Evaluation
While in the private mode, Google Chrome left no browsing artifacts in any of the “common” and “uncommon” locations on the hard drive. Consistent with Google Chrome, although Mozilla Firefox, while in private mode, avoided leaving browsing artifacts in the majority of locations, nevertheless it spread artifacts into one “common” location, the Download folder, and two “uncommon” locations, namely places.sqlite and ieframe.dll.mui. Analysis of these locations revealed traces of all of the pre-defined browsing activities performed in the private mode session, with the exception of the search terms “Jessie ware wildest moments”, “Casio F-91 W” and “Doppelganger: Better Browser privacy without the Bother.” In contrast, the number of locations in which Internet Explorer stored artifacts while in private browsing mode was astonishing. These entries represented traces of the entirety of the pre-defined web browsing activities performed. While in the “private” mode, Internet Explorer had stored browsing artifacts in “common” and “uncommon” locations such as Web History, Cache, ieframe.dll.mui, ntuser.dat, pagefile.sys, schema.dat, search.js, $MFT, $Logfile and $Unalloc and “e4e8be02b8faeta7_blobs.bin”. Apple Safari, whilst in “private” mode, avoided leaving artifacts in most of those locations, leaving them in only one “common” location, Download folder, and three “uncommon” locations, “e4e8be02b8faeta7_blobs.bin”, “$Unalloc”, “WebpageIcons.db”.
5.2 Comparison
5.2.1 Common and Uncommon Locations
This sub-section compares and evaluates the “private” browsing modes of the four web browsers based upon the results of the analysis of the “common” and “uncommon” locations on the Hard Drive. Based on the figures in Tables 9 and 10, “Incognito” of Google Chrome is the most secure and private of the private browsing modes. Google Chrome left no browsing artifact from its “private” browsing session in the “common” and “uncommon” locations on the hard drive. These results accord with Google’s claims that, “Web pages that you open and files downloaded while you are in Incognito aren’t recorded in your browsing and download histories.” [1]. Moreover, “Incognito” can be regarded as a “secure” and “private” mode based upon the definition of Aggarwal et al’s [8] first goal of private modes, the “local attacker model”. Aggarwal et al. [8] state that for a web browser’s private mode to be considered “secure” it must provide security against a “local attacker” (a forensic examiner or user of the same machine) by not leaving any browsing artifact in any location on the hard drive while in “private” mode.
Although Mozilla Firefox leaked browsing artifacts from its “private” browsing session to some locations on the hard drive, the number of such locations was low, amounting to two “uncommon” locations and only one “common” location. The experiments therefore demonstrated that Mozilla Firefox offers the second most secure web browser, the first being Google Chrome. However, based upon the “local attacker model” [8], Firefox’s “private” mode cannot be regarded as a “secure” and “private” mode, leaking some artifacts into locations on the hard drive which could be accessed by a forensic investigator. Therefore, Mozilla Firefox must not be regarded as a private browser due to the fact that browsing artifacts can be seen, albeit in relatively few locations. Such findings appear to be in contradiction with the claims of Mozilla that, “Private Browsing allows you to browse the Internet without saving any information about which sites and pages you’ve visited.” [3].
In contrast to Google Chrome and Mozilla Firefox, traces of the entirety of the pre-defined browsing activities carried out in Internet Explorer’s “InPrivate” mode were recovered from both “common” and “uncommon” locations on the hard drive. As Tables 9 and 10 highlight, the results of the experiments in the private browsing mode of Internet Explorer are astonishing. For example, while in private mode, Internet Explorer leaves browsing artifacts in many locations on the hard drive. The conclusion is that Internet Explorer offers no privacy at all. Therefore, Internet Explorer’s private mode does not meet the criteria of the “local attacker model” in [8]. The results for private browsing using Internet Explorer are in conflict with the claims of Microsoft that, “InPrivate Browsing helps prevent your browsing history and temporary Internet files from being retained by the browser.” [1].
Consistent with Internet Explorer’s “private” browsing mode, Apple Safari also leaked onto the hard drive traces of all pre-defined web browsing activities carried out during its “private” session. However, based upon the figures in Tables 9 and 10, Apple Safari would appear to be more secure and private than Internet Explorer. For example, Internet Explorer left artifacts in many “common” and “uncommon” locations, whereas, Apple Safari left them in only one “common” location and three “uncommon” locations. Nevertheless, Apple Safari’s private mode cannot still be regarded as “private” and “secure” based upon the “local attacker model” in [8], which asserts that in order for a private mode to be regarded as “private”, it must provide security against a “local attacker” by leaving no browsing artifact in any location on the hard drive. It can be concluded that Apple does not fulfill the promises made to users in stating:
When Private Browsing is on, web pages are not added to the history list, the names of downloads are removed from the Downloads window, and searches are not added to the search field’s pop-up menu [4].
5.3 Physical Memory
This sub-section compares and evaluates the private browsing modes of the four web browsers based upon the results of the analysis of the “Physical Memory” (RAM). Table 8 provides the total number of entries discovered in “Physical Memory” (RAM) for each pre-defined activity carried out in the private browsing mode of the four web browsers. As Table 8 demonstrates, an analysis of the captured image of the “Physical Memory” (RAM) for each “private” mode reveals that each web browser’s “private” mode places in the RAM a significant number of entries relating to the browsing activities. In those circumstances, it would not be appropriate to compare the number of entries to conclude which is the safest “private” mode as the deposit of so many artifacts in the RAM thoroughly undermines the privacy offered by each of the four web browsers, even Google Chrome, which is considered to be secure and private.
The results of the analysis of the RAM for “private” browsing activities carried out for this project accord with those of other forensic experts, including [8, 11, 12]. These forensic experts all agree that private browsing artifacts can be recovered from RAM as erasing all volatile memory after exiting the private mode is difficult for private browsers to achieve. However, the opinions of forensic experts then diverge. Said et al. [12] believe that forensic experts would be able to acquire data from RAM even if the user had exited the private mode session, provided that the computer was still running. In contrast, Aggarwal et al. [8] believe that a forensic investigator would be able to retrieve data only if he/she was able to access the suspect’s computer before the private mode session was terminated. Aggarwal et al. [8] do state that although most of these artifacts are erased from the volatile memory once the user exits the private mode, the investigator could nevertheless find some artifacts even after exiting the private mode, as erasing all private browsing data from volatile memory is difficult to achieve.
The assertions of Aggarwal et al. [8] appear to be the more valid, being supported by others such as [11]. Aggarwal et al’s [8] arguments are also supported by the experiments carried out in this project, where “private” browsing artifacts were recovered from RAM by imaging the RAM before closing down the “private” mode and shutting down the computer. Consequently, digital forensic investigators are advised to take advantage of “live” examinations, imaging and analyzing the RAM which has proved to be a rich source of browsing artifacts. Furthermore, there are cases where “private” browsing data left in the RAM was retrieved despite the fact that the computer was turned off after the termination of the “private” mode session. An “uncommon” location on the hard drive behaves as though it were the RAM in order to store data that RAM cannot accommodate when fully used. This “uncommon” location on the hard drive accommodating data from RAM is called the “pagefile.sys” file. This was confirmed in the experiments conducted for this project, the “pagefile.sys” file providing a substantial source of browsing artifacts in both the “public” and “private” browsing modes. For example, browsing artifacts were left in this “uncommon” location by all four of the web browsers. Internet Explorer alone placed browsing artifacts from the “private” browsing session in this file. Accordingly, based on its significant benefits for recovering browsing data, forensic investigators are recommended to examine this file to retrieve evidential artifacts left from “private” browsing sessions. However, this method is not infallible as a suspect with a good understanding of digital forensic techniques could manually erase from the memory any browsing artifact left from a “private” session.
6 Conclusion and Future Work
This project analyzed the effectiveness of the “private” modes of four widely deployed web browsers, resulting in the discovery of numerous weaknesses in their implementation which preclude them from meeting their desired security goals. As regards the “local attacker model”, experiments carried out in this project exposed the reality that the “private” browsers of Mozilla Firefox, Internet Explorer and Apple Safari cannot keep browsing activities private from a local attacker, such as a forensic examiner. All three left behind various types of browsing data in both “common” and “uncommon” locations on the hard drive. Consequently, although the “private” modes of Mozilla Firefox, Internet Explorer and Apple Safari might offer regular users some degree of privacy against other regular users of the same machine at a local level of Internet information, they cannot conceal the user’s private browsing activity from a dedicated computer forensic expert. Therefore, the level of privacy provided by these three major browsers is at best sufficient for only the average user. In contrast, this project’s experiments on the “private” browsing mode of Google Chrome revealed that it is completely private, not leaving any browsing artifact in either “common” or “uncommon” locations on the hard drive. These results conflict with the results achieved by Said et al. [12], where Google Chrome is disregarded as a completely private mode. However, this could be explained by the fact that Said et. al’s [12] experiment was conducted on an older version of Google Chrome. It is important to note that all four web browsers leave behind “private” browsing artifacts in the “Physical Memory” (RAM). Therefore, on seizing a suspect’s computer whilst it is still turned on, a forensic examiner could recover from the RAM all browsing activities carried out during the “private” browsing session. The opportunity to recover such data if a computer is seized after the machine is turned off is greatly reduced, as the volatile nature of RAM may cause the data to be lost.
A dedicated computer forensic investigator is able to recover many forensic browsing artifacts by using effective forensic tools and techniques. This contradicts the professed advantages of “private” modes, making it arguable that “private” modes are not in reality private at all. Nevertheless, the prospect of reconstructing the suspicious behaviour of a person using a “private” mode is dependent on the variety of the “private” browser used and the skills of both the forensic investigator and suspect. For example, a forensic investigator would more easily retrieve evidential artifacts from a computer where a suspect had utilized the “private” modes of Internet Explorer or Apple Safari rather than Mozilla Firefox, as they are less secure. The difficulty of recovery increases in proportion to the suspect’s knowledge of digital forensic techniques and tools, such as the methods of manually deleting any remaining data not effectively removed by the browser. However, even where a suspect had no such knowledge, a forensic investigator would be unable to recover “private” browsing data where Google Chrome had been used, as no such data is left in Google Chrome’s “private” mode.
Future work should be extended to investigate the browser add-ons to determine whether these add-ons undermine the security of “private” browsers by leaking data onto the hard drive. This has not been verified by any experiment, being outside of the scope of this project.